Page 75 - 2024F
P. 75
68 UEC Int’l Mini-Conference No.53
Evolutionary Multi Objective Transfer Optimization
Authors: Hiroyuki Sato, Del Valle Fermin
UEC Exchange Study Program (JUSST Program)
Department of Informatics, Hiroyuki Sato Laboratory
delvallevegaferminalberto@gmail.com
Introduction Flowchart
The growing need for secure and efficient storage and transmission of digital audio Start: Audio Input.
data necessitates advanced Audio Preprocessing. (DCT applied)
algorithms that can handle both encryption and compression simultaneously. This
Compression & Encryption. (Compressive Sensing Key k1)
work presents the implementation
Chaotic Mixing. (Whit keys k2 & k3)
of the Non-Dominated Sorting Genetic Algorithm II (NSGA-II) integrated with
Compressive Sensing (CS) NSGA-II Optimization.
and Chaotic Mixing for secure audio processing (Donoho, 2006; Eldar & Kutiniok, Decryption & Reconstruction.
2012).
Calculate Metrics. (PCC, Variance)
Algorithm Overview: NSGA-II
Experimental Analysis.
(Waveform, Spectrogram, Histogram)
NSGA-II is a multi-objective optimization algorithm used to optimize two primary Results & Findings.
objectives in this implementation:
Figure 1: Flowchart of the NSGA-II Algorithm.
Maximizing Randomness: Ensuring the encrypted signal resembles white Spectrogram Analysis
noise.
Minimizing Correlation: Reducing the correlation between the original and
encrypted signals.
The algorithm evolves populations across generations to find Pareto-optimal
solutions balancing these objectives
(Candes et al., 2006).
System Architecture
Audio Preprocessing
Input: An audio file.
The audio is segmented into frames of size N.
Each frame is transformed into a sparse representation using the Discrete
Cosine Transform (DCT) (Parkale & Nalbalwar, 2017).
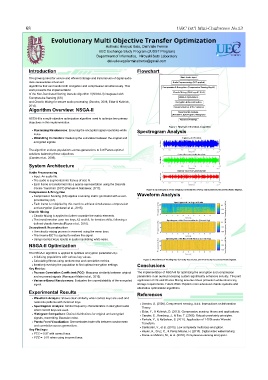
Figure 2: Spectrograms of the Original, Correctly Recovered, and Incorrectly Recovered Audio Signals.
Compression & Encryption
Compressive Sensing (CS) applies a sensing matrix generated with a user- Waveform Analysis
provided key (k1).
Each frame is multiplied by this matrix to achieve simultaneous compression
and encryption (Cambareri et al., 2015).
Chaotic Mixing
Chaotic Mixing is applied to further scramble the matrix elements.
The transformation uses two keys, k2 and k3, for iterative shifts, following a
defined chaotic formula (Reyes et al., 2010).
Decryption & Reconstruction
The chaotic mixing process is reversed using the same keys.
The inverse DCT is applied to restore the signal.
Using incorrect keys results in audio resembling white noise.
NSGA-II Optimization
The NSGA-II algorithm is applied to optimize encryption parameters by:
Initializing populations with various key values.
Calculating fitness using randomness and correlation metrics. Figure 3: Waveforms of the Original, Correctly Recovered, and Incorrectly Recovered Audio Signals.
Iteratively evolving the population to find optimal encryption settings. Conclusions
Key Metrics:
Pearson Correlation Coefficient (PCC): Measures similarity between original The implementation of NSGA-II for optimizing the encryption and compression
and recovered signals (Ramezani-Matimi et al., 2018). parameters in an audio processing system significantly enhances security. The joint
Variance-Based Randomness: Evaluates the unpredictability of the encrypted application of CS and Chaotic Mixing ensures robust protection while minimizing
signal. storage requirements. Future Work: Explore more advanced chaotic systems and
alternative optimization algorithms.
Experimental Results
References
Waveform Analysis: Shows clear similarity when correct keys are used and
noise-like patterns with incorrect keys.
Donoho, D. (2006). Compressed sensing. IEEE Transactions on Information
Spectrogram Analysis: Similar frequency characteristics in decrypted audio
Theory.
when correct keys are used.
Eldar, Y., & Kutiniok, G. (2012). Compressive sensing: theory and applications.
Histogram Comparison: Distinct distributions for original and encrypted
Candes, E., Romberg, J., & Tao, T. (2006). Robust uncertainty principles.
signals, resembling Gaussian noise.
Parkale, Y., & Nalbalwar, S. (2017). Application of 1-D Discrete Wavelet
Pareto Front Visualization: Demonstrates trade-offs between randomness
Transform.
and correlation across generations.
Cambareri, V., et al. (2015). Low complexity multiclass encryption.
Key Findings:
Reyes, R., Cruz, C., & Perez-Meana, H. (2010). Digital video watermarking.
PCC ≈ 0.97 with correct keys.
Ramezani-Matimi, M., et al. (2018). Compressive sensing encryption.
PCC ≈ 0.01 when using incorrect keys.