Page 81 - 2024F
P. 81
74 UEC Int’l Mini-Conference No.53
Data hiding components for solving information security
issues in DICOM medical images.
Eng. Juan Eduardo Mosco Garcia, Ph.D. Hayaru Shouno,
Department of Informatics
University of Electro-Communications
Tokyo, Japan
m2495010@gl.cc.uec.ac.jp, shouno@uec.ac.jp
EXPERIMENTAL RESULTS
INTRODUCTION
Current Context: With the rise of new technologies, the risks of information
manipulation have become increasingly common, making it necessary to
implement stricter security measures. One example can be found in mobile
devices, where systems like Apple Intelligence and Galaxy AI modify the
metadata of manipulated images, indicating that they have been generated
or edited using artificial intelligence. These techniques are not limited to
ordinary photographs but also extend to more sensitive information, such as (a) (b)
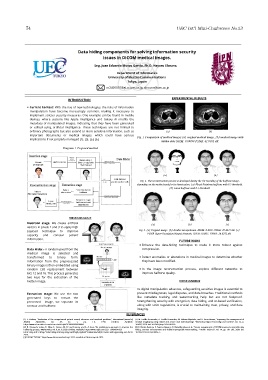
important documents or medical images, which could have serious Fig. 1 Comparison of medical images (a) original medical image, (b) medical image with
implications if not properly managed [1], [3], [5], [6].
hidden data SSIM: 0.99999 PSNR: 81.0382 dB.
Diagram. 1 Proposed method
(a) (b)
Fig. 2. The reconstruction process is developed during the 1/4 rescaling of the halftone image,
depending on the method used for its binarization. (a) Floyd-Steinberg halftone with 0.5 threshold.
(b) Jarvis halftone with 0.5 threshold.
METHODOLOGY
Insertion stage. We create artificial (a) (b) (c)
vectors in pixels 1 and 3 to apply high
payload technique to improve Fig. 3. (a) Original Image. (b) Bicubic Interpolation. SSIM: 0.8945 PSNR: 29.4273 dB. (c)
capacity and conceal patient VDSR Super-Resolution Neural Network. SSIM: 0.8851, PSNR: 26.0272 dB.
information.
FUTURE WORK
Enhance the data-hiding technique to make it more robust against
Data Hider.- A random pixel from the compression.
medical image is selected and
transformed to binary form. Detect anomalies or alterations in medical images to determine whether
Information from the preprocessed they have been modified.
binary image is then embedded using
random LSB replacement between In the image reconstruction process, explore different networks to
bits 12 and 16. This process generates improve halftone quality.
two keys for the extraction of the
hidden image. CONCLUSIONS
As digital manipulation advances, safeguarding sensitive images is essential to
Extraction stage: We use the two prevent misdiagnoses, legal disputes, and data breaches. Traditional methods
generated keys to extract the like metadata tracking and watermarking help but are not foolproof.
precessed image, we separate its Strengthening security with encryption, data hiding, and AI-based verification,
contour and halftone. along with strict regulations, is crucial to maintaining trust, privacy, and data
integrity.
REFERENCES
[1] S. Kaihara, “Realisation of the computerised patient record; relevance and unsolved problems,” International Journal of [5] M. Cedillo-Hernandez, A. Cedillo-Hernandez, M. Nakano-Miyatake, and H. Perez-Meana, “Improving the management of
Medical Informatics, vol. 49, no. 1, pp. 1–8, 1998. [Online]. Available: medical imaging by using robust and secure dual watermarking,” *Biomedical Signal Processing and Control*, vol. 56, p.
https://www.sciencedirect.com/science/article/pii/S1386505698000045 101695, 2020. doi: 10.1016/j.bspc.2019.101695.
asdasd
[2] N. Ortega-Sa ́ nchez, D. Oliva, E. Cuevas, M. Pe ́ rez-Cisneros, and A. A. Juan, “An evolutionary approach to improve the [6] D. Nuñez-Ramirez, E. Fragoso-Navarro, D. Mata-Mendoza, et al., “Secure management of DICOM images via reversible data
halftoning process,” Mathematics, vol. 8, no. 9, 2020. [Online]. Available: https://www.mdpi.com/2227-7390/8/9/1636 hiding, contrast enhancement and visible-imperceptible watermarking,” *Health Technol.*, vol. 14, pp. 581–596, 2024. doi:
[3] W. Ding and Y. Wang, “Data hiding in binary image with high payload,” Arabian Journal for Science and Engineering, vol. 43, 03 10.1007/s12553-024-00856-5.
2018.
[4] DICOM, “DICOM,” https://www.dicomstandard.org/, 2024, accedido el 16 de mayo de 2024.