Page 77 - 2024S
P. 77
70 UEC Int’l Mini-Conference No.52
Realization of Secure Communication in
Low-power RISC-V System-on-Chips for IoT Applications
Tuan-Kiet DANG (tuankiet@vlsilab.ee.uec.ac.jp), Trong-Thuc HOANG, Cong-Kha PHAM
The University of Electro-Communications (UEC), Tokyo, Japan
I. INTRODUCTION
In an Internet-of-Thing network, security is a crucial aspect of communication between numerous sensor devices and the server. A safe communication
channel reduces the risk of eavesdropping and tampering with the sensor data from unauthenticated parties. Moreover, a highly secure communication
protocol ensures data integrity and privacy in a massive network. However, IoT endpoint devices, as their nature, are limited in resources and computation
efficiency, meanwhile, the mathematical foundation of highly secure communication demands extensive computational costs. Following the trend of applying
free and open-source computer architecture, this research aims to develop a well-rounded RISC-V system to leverage the cost of secure communication and
low power demands for IoT devices. To achieve the target, problems to be solved include: (a)research for a lightweight approach for secure communication
(b)developing robust and low-cost cryptography primitives (TRNG, PUF, etc.), (c)reducing the computation cost of cryptography algorithms, (d)connecting the
pieces to create a trusted execution environment.
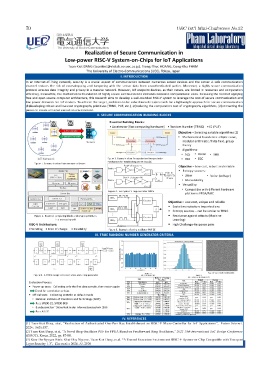
II. SECURE COMMUNICATION BUILDING BLOCKS
Essential Building Blocks:
• Accelerator (fast computing hardware) • Random Number (TRNG) • ID (PUF)
Objective – Selecting suitable algorithms [2]
Mathematical foundation: elliptic curve,
modular arithmetic, finite field, group
theory
Algorithms:
• AES • Ascon • SHA
Figure 3. Example of an Encapsulation-Decapsulation • RSA • ECC
mechanism for establishing secret keys [1]
Figure 1. Communication from sensors to Server
Objective – Low-cost, robust and reliable
Entropy sources:
• Jitter • Noise (voltage)
• Metastability
Versatility:
• Compatible with different hardware
Figure 4. Example of a ring oscillator TRNG
platforms FPGA/ASIC
Objective – Low-cost, unique and reliable
Exploit manufacture imperfections
Entropy sources – can be similar to TRNG
Figure 2. Essential computing blocks and crypto-primitives Resistance against attacks (Machine
in a processing unit Learning)
RISC-V Architecture: High Challenge-Response pairs
•Trending • Free of charge • Flexibility Figure 5. Example of a ring oscillator PUF [3]
III. TRUE RANDOM NUMBER GENERATOR CRITERIA
Raw bit map of 1Mbit (1000x1000)
Figure 6. A TRNG design with oscillators and a ring generator
Evaluation Process:
Power-up tests: Collecting only the first data sample, then restart again
Check for correlation or bias
Official tests: Collecting 100Mbit at default mode
• National Institute of Standards and Technology (NIST)
Pass SP800-22, SP800-90B
• Bundesamt fur ¨ Sicherheit in der Informationstechnik (BSI)
Pass AIS-31
IV. REFERENCES
[1] Tuan-Kiet Dang, et.al, “Realization of Authenticated One-Pass Key Establishment on RISC-V Micro-Controller for IoT Applications”, Future Internet.
2024; 16(5):157.
[2] Tuan-Kiet Dang, et.al, "A Novel Ring Oscillator PUF for FPGA Based on Feedforward Ring Oscillators," 2022 19th International SoC Design Conference
(ISOCC), Korea, 2022, pp. 87-88.
[3] Kieu-Do-Nguyen Binh; Khai-Duy Nguyen, Tuan-Kiet Dang, et.al, “A Trusted Execution Environment RISC-V System-on-Chip Compatible with Transport
Layer Security 1.3”, Electronics 2024, 13, 2508